Dealing with PDF forms online is certainly very simple using our PDF editor. Anyone can fill out application form here within minutes. FormsPal team is committed to providing you the perfect experience with our tool by regularly releasing new features and enhancements. Our editor has become a lot more intuitive as the result of the most recent updates! Now, working with PDF documents is a lot easier and faster than ever before. With just a couple of simple steps, you can start your PDF journey:
Step 1: Simply click the "Get Form Button" at the top of this webpage to start up our pdf form editor. There you'll find everything that is necessary to fill out your file.
Step 2: With the help of our online PDF tool, you're able to do more than merely complete blank form fields. Express yourself and make your docs look professional with customized textual content added in, or modify the file's original input to excellence - all that backed up by the capability to incorporate stunning images and sign the document off.
When it comes to blank fields of this specific document, here is what you need to know:
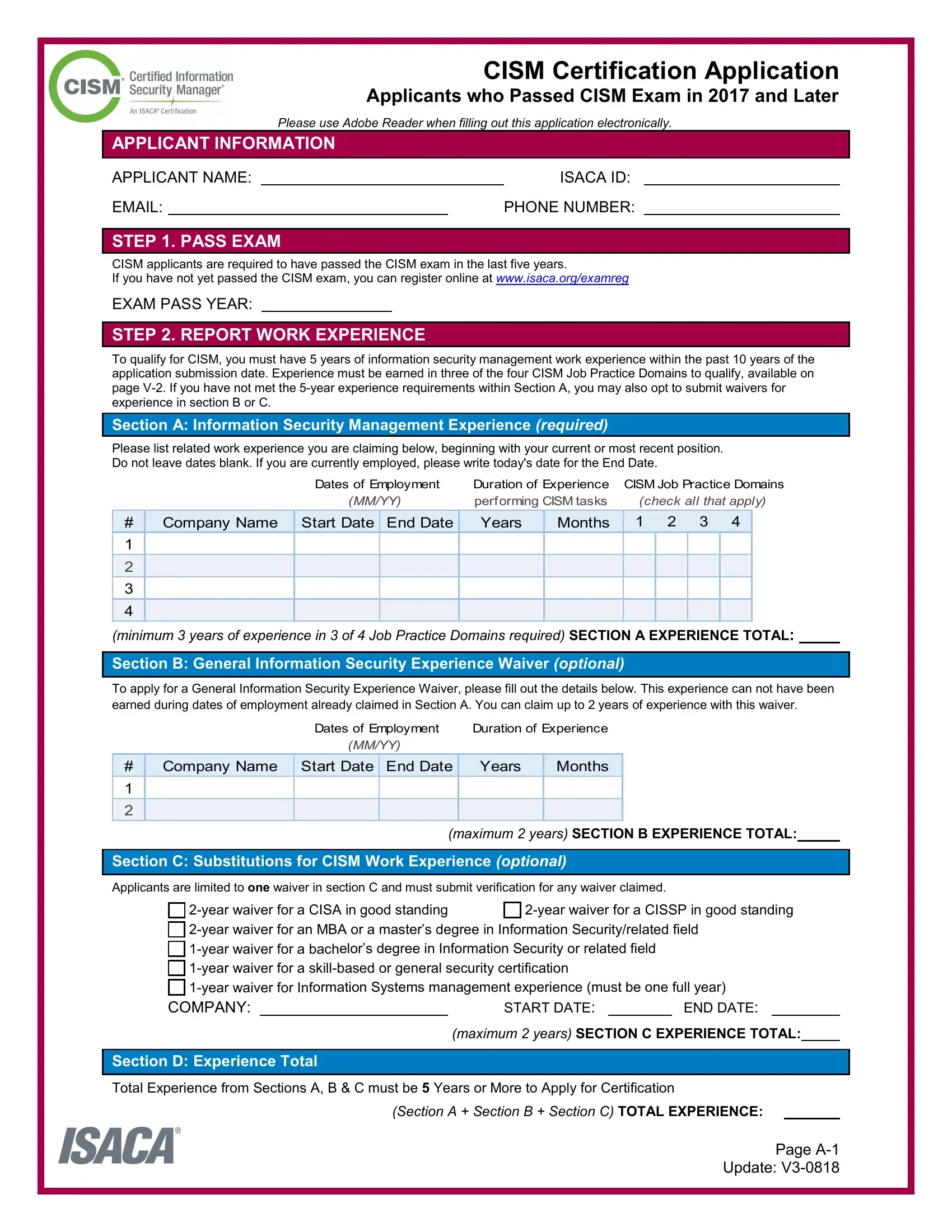
1. The application form involves specific information to be typed in. Make certain the following fields are completed:
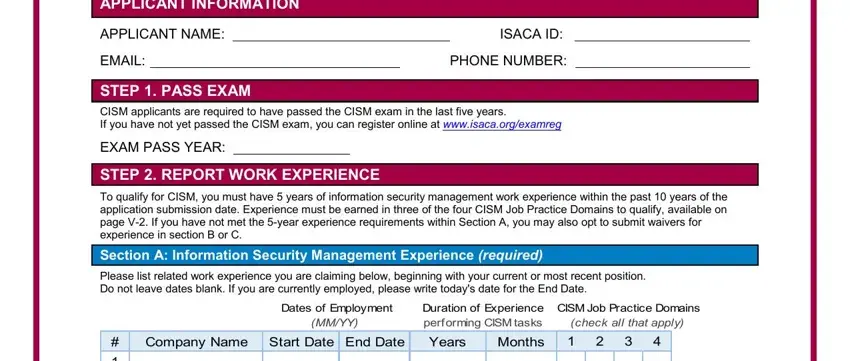
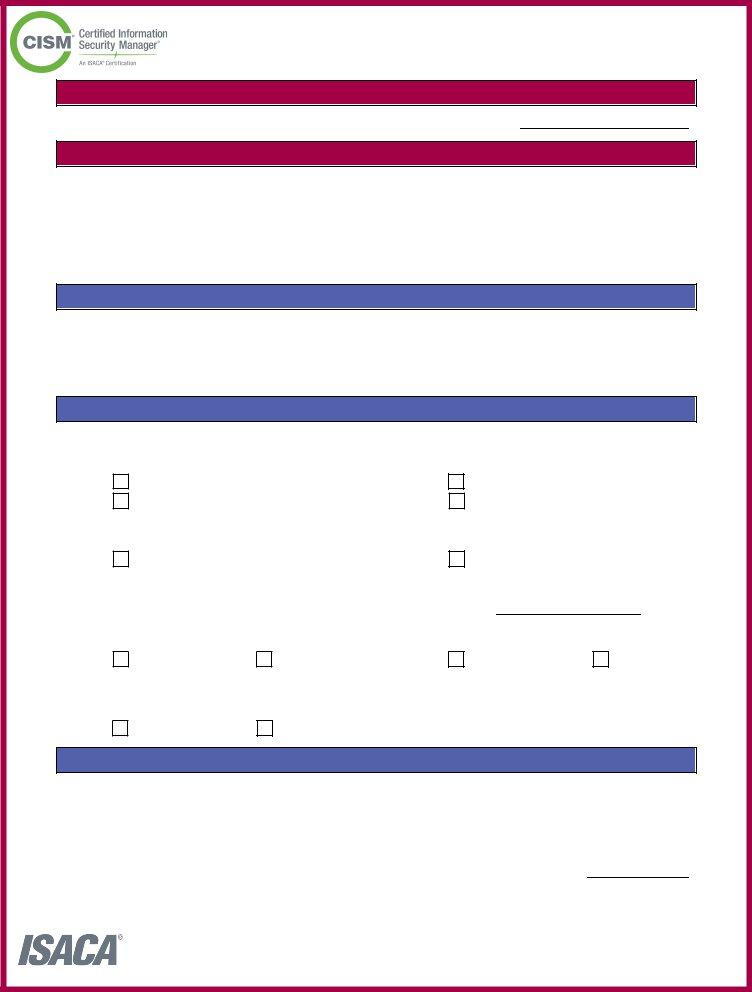
2. After this part is filled out, go to enter the applicable information in all these: minimum years of experience in , Section B General Information, To apply for a General Information, Dates of Employment, Duration of Experience, MMYY, Company Name, Start Date End Date, Years, Months, Section C Substitutions for CISM, Applicants are limited to one, maximum years SECTION B, year waiver for a CISA in good, and year waiver for a CISSP in good.
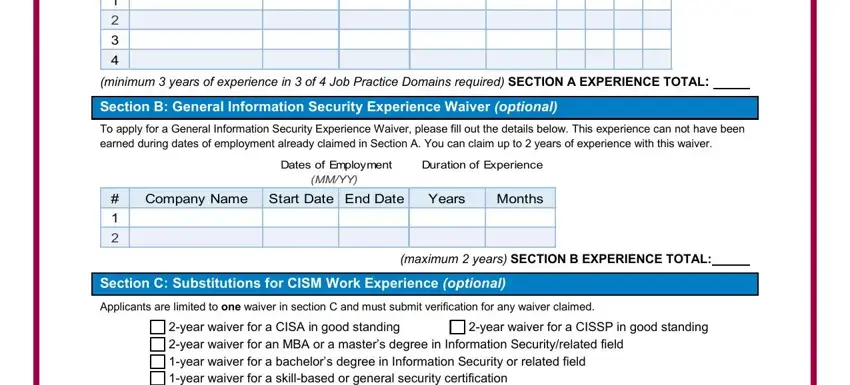
Be very mindful while filling in Section C Substitutions for CISM and MMYY, since this is the section in which most people make a few mistakes.
3. The next part is going to be straightforward - fill in every one of the blanks in year waiver for a CISA in good, COMPANY, START DATE, END DATE, maximum years SECTION C, Section D Experience Total, Total Experience from Sections A B, Section A Section B Section C, and Page A Update V in order to complete this part.
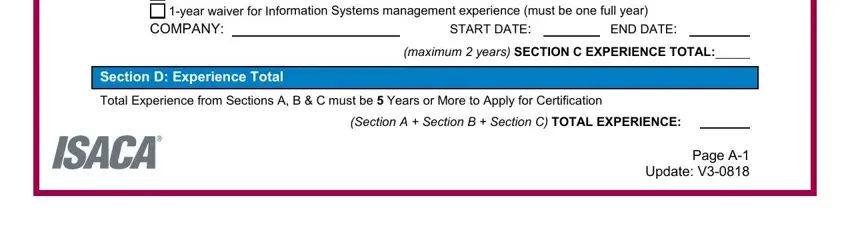
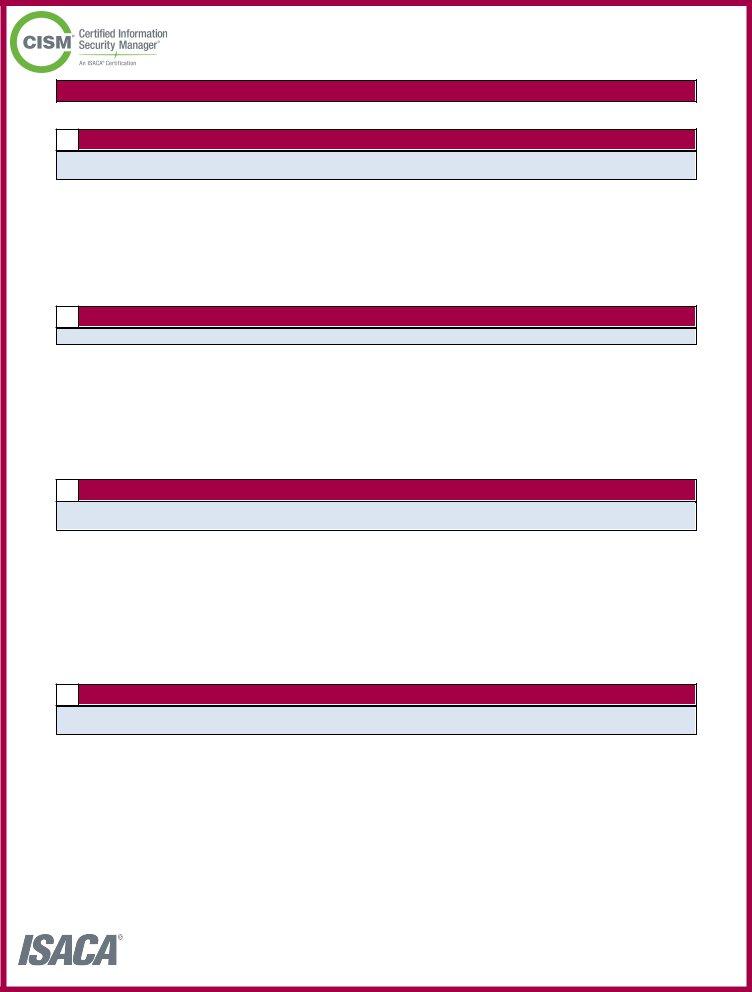
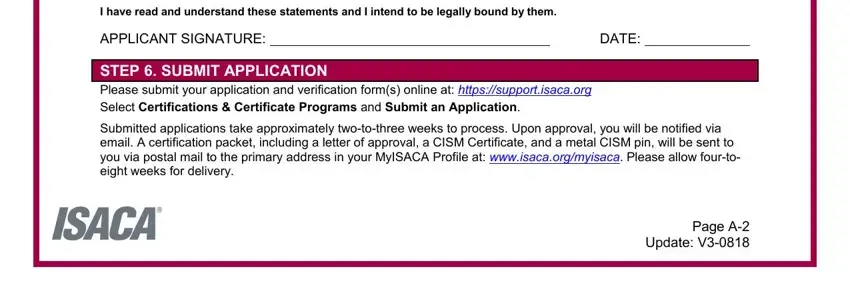
4. This next section requires some additional information. Ensure you complete all the necessary fields - I have read and understand these, APPLICANT SIGNATURE, DATE, STEP SUBMIT APPLICATION Please, Submitted applications take, and Page A Update V - to proceed further in your process!
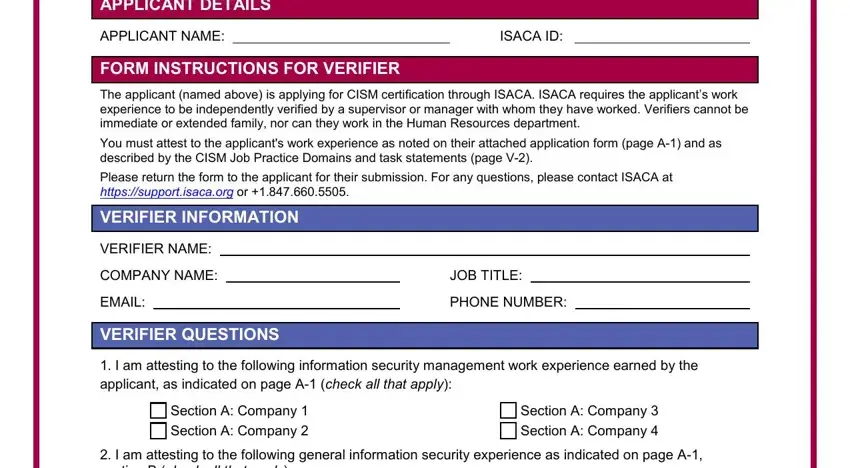
5. The pdf needs to be finished within this section. Below there's a full listing of fields that need to be filled in with accurate details for your document submission to be accomplished: APPLICANT DETAILS, APPLICANT NAME, FORM INSTRUCTIONS FOR VERIFIER, ISACA ID, The applicant named above is, You must attest to the applicants, Please return the form to the, VERIFIER NAME, COMPANY NAME, EMAIL, VERIFIER QUESTIONS, JOB TITLE, PHONE NUMBER, I am attesting to the following, and Section A Company Section A.
Step 3: Check the details you've inserted in the blanks and then hit the "Done" button. Go for a 7-day free trial account at FormsPal and obtain immediate access to application form - download or edit in your personal account. FormsPal offers safe form editor with no personal data recording or any sort of sharing. Be assured that your details are in good hands with us!