FFIEC Cybersecurity Assessment Tool |
User’s Guide |
By reviewing both the institution’s inherent risk profile and maturity levels across the domains,
management can determine whether its maturity levels are appropriate in relation to its risk. If
not, the institution may take action either to reduce the level of risk or to increase the levels of maturity. This process is intended to complement, not replace, an institution’s risk management
process and cybersecurity program.
Background
The Assessment is based on the cybersecurity assessment that the FFIEC members piloted in
2014, which was designed to evaluate community institutions’ preparedness to mitigate cyber risks. NIST defines cybersecurity as “the process of protecting information by preventing, detecting, and responding to attacks.” As part of cybersecurity, institutions should consider
managing internal and external threats and vulnerabilities to protect infrastructure and information assets. The definition builds on information security as defined in FFIEC guidance.
Cyber incidents can have financial, operational, legal, and reputational impact. Recent high- profile cyber attacks demonstrate that cyber incidents can significantly affect capital and earnings. Costs may include forensic investigations, public relations campaigns, legal fees, consumer credit monitoring, and technology changes. As such, cybersecurity needs to be
integrated throughout an institution as part of enterprise-wide governance processes, information security, business continuity, and third-party risk management. For example, an institution’s
cybersecurity policies may be incorporated within the information security program. In addition, cybersecurity roles and processes referred to in the Assessment may be separate roles within the security group (or outsourced) or may be part of broader roles across the institution.
Completing the Assessment
The Assessment is designed to provide a measurable and repeatable process to assess an institution’s level of cybersecurity risk and preparedness. Part one of this Assessment is the
Inherent Risk Profile, which identifies an institution’s inherent risk relevant to cyber risks. Part two is the Cybersecurity Maturity, which determines an institution’s current state of
cybersecurity preparedness represented by maturity levels across five domains. For this Assessment to be an effective risk management tool, an institution may want to complete it periodically and as significant operational and technological changes occur.
Cyber risk programs build upon and align existing information security, business continuity, and disaster recovery programs. The Assessment is intended to be used primarily on an enterprise- wide basis and when introducing new products and services as follows:
Enterprise-wide. Management may review the Inherent Risk Profile and the declarative statements to understand which policies, procedures, processes, and controls are in place enterprise-wide and where gaps may exist. Following this review, management can determine appropriate maturity levels for the institution in each domain or the target state for Cybersecurity Maturity. Management can then develop action plans for achieving the target state.
New products, services, or initiatives. Using the Assessment before launching a new product, service, or initiative can help management understand how these might affect the institution’s inherent risk profile and resulting desired maturity levels.






 FFIEC Cybersecurity Assessment Tool
FFIEC Cybersecurity Assessment Tool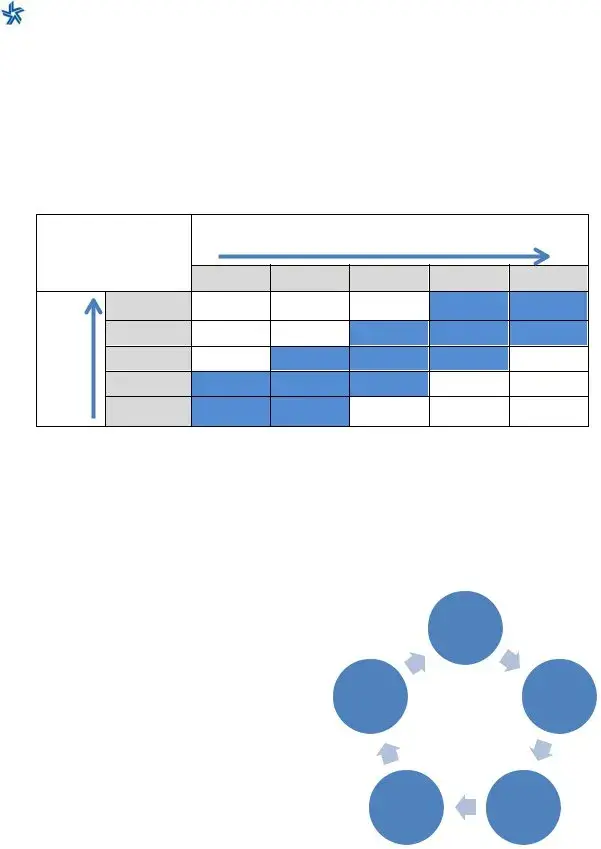

 FFIEC
FFIEC



