You are able to fill in 2013 without difficulty in our PDFinity® editor. To make our editor better and easier to work with, we consistently develop new features, taking into consideration suggestions from our users. Getting underway is effortless! Everything you need to do is follow the following basic steps down below:
Step 1: Hit the "Get Form" button in the top section of this page to get into our tool.
Step 2: With our online PDF editing tool, it is easy to accomplish more than simply complete blank fields. Express yourself and make your docs appear faultless with customized textual content added in, or modify the file's original content to perfection - all accompanied by an ability to incorporate almost any images and sign it off.
Completing this PDF needs attentiveness. Ensure all necessary areas are filled in properly.
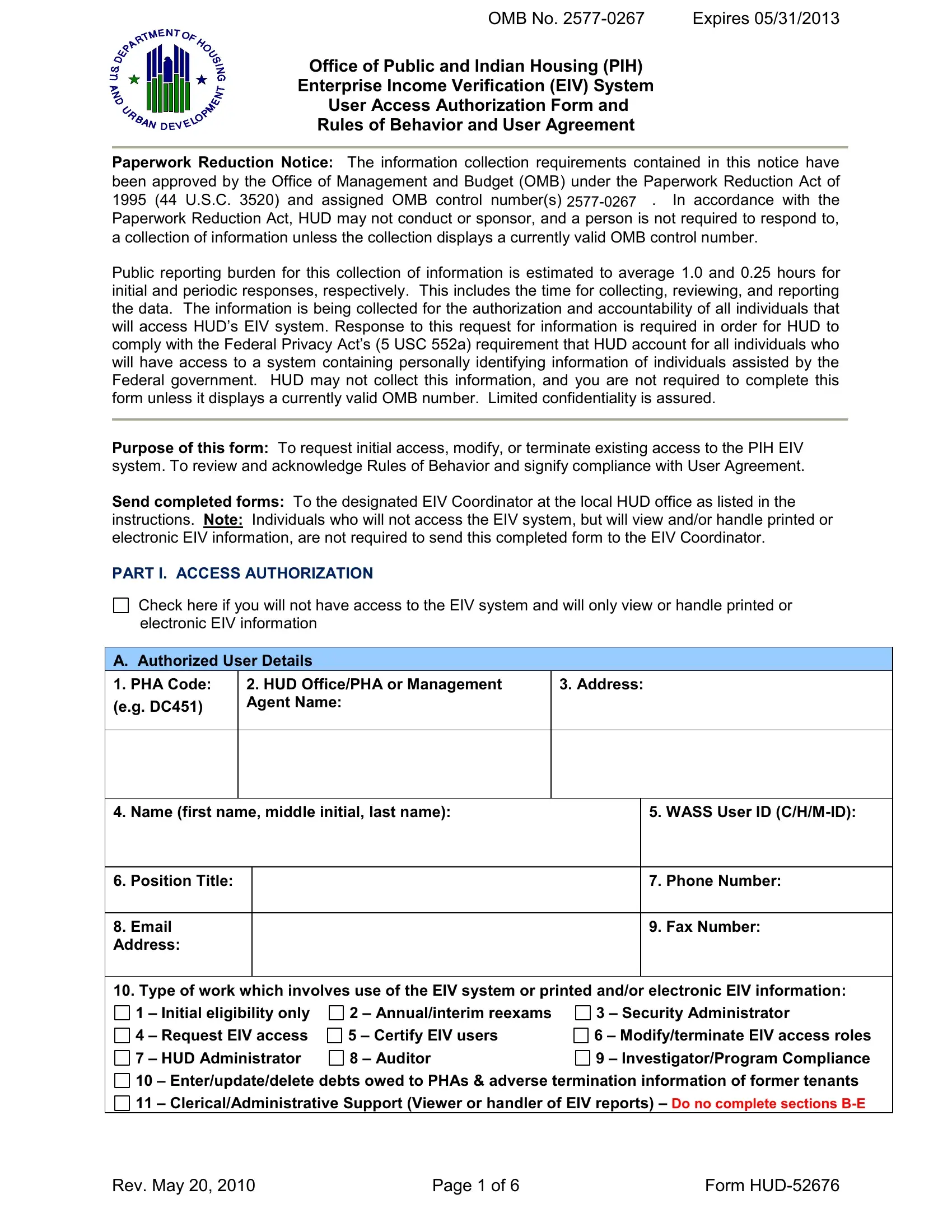
1. Whenever completing the 2013, be certain to include all of the important fields in its associated form section. It will help speed up the process, which allows your information to be handled quickly and properly.
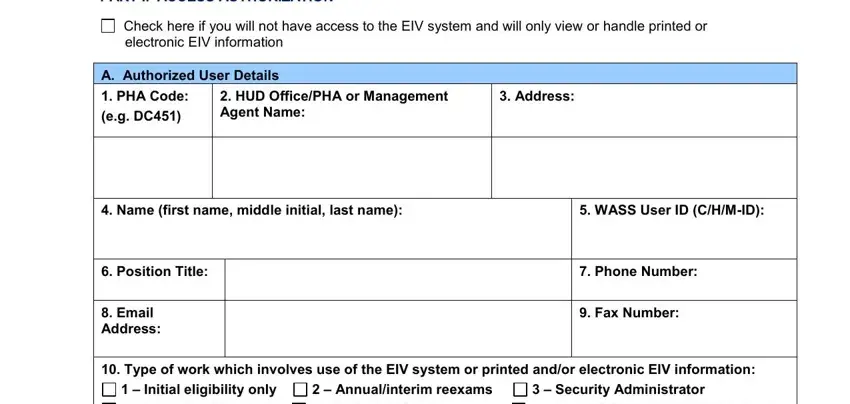
2. Once your current task is complete, take the next step – fill out all of these fields - Initial eligibility only, Security Administrator, Annualinterim reexams Certify, Rev May, Page of, and Form HUD with their corresponding information. Make sure to double check that everything has been entered correctly before continuing!

3. Completing B Type of Action Requested See, PHA Occupancy Public Housing, Program Administrator Voucher, D Public Housing Portfolio Specify, Check here to grant access to all, Project Number, Project Number, Project Number, E HUD User Access Roles Internal, Occupancy Specialist Security, and HQ PIH DHAP HQ System is essential for the next step, make sure to fill them out in their entirety. Don't miss any details!
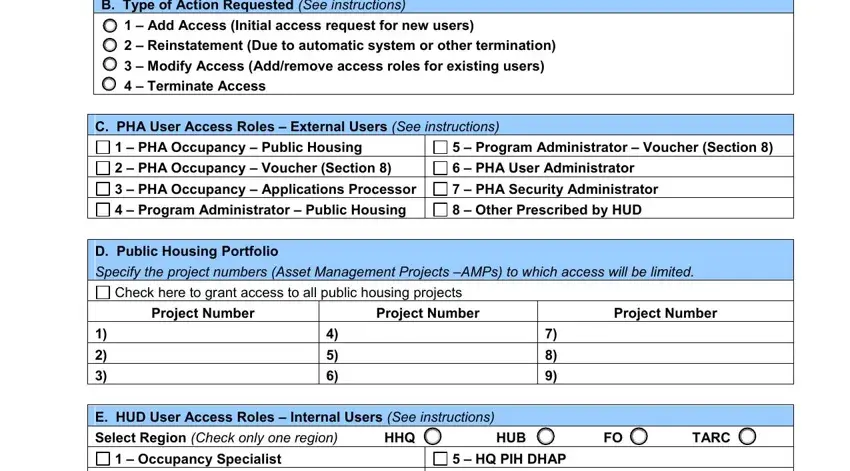
4. The fourth part arrives with these particular empty form fields to enter your particulars in: Occupancy Specialist Security, F Authorization, HQ PIH DHAP HQ System, As the Authorizing Official I, Authorizing Officials Name Print, Authorizing Officials Signature, Date, Check here for ELECTRONIC, subject to inspection, G For HUD Use Only Maintain a copy, HUD EIV Coordinators Name, and Action taken Approved Denied Reason.
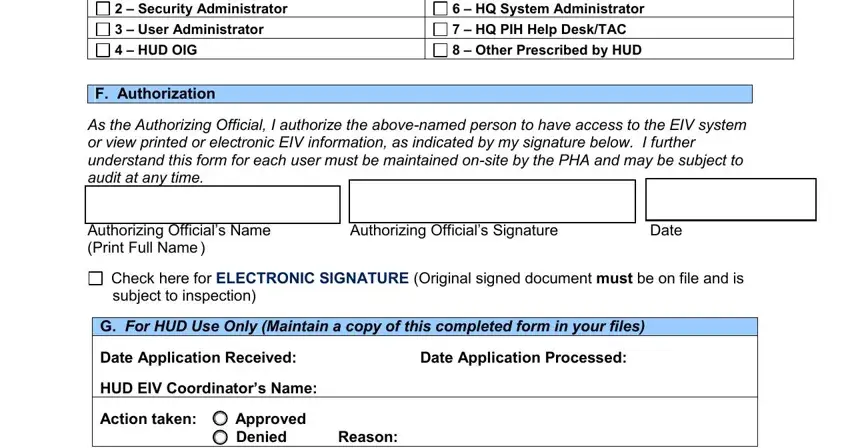
People who use this form generally make errors while filling out HQ PIH DHAP HQ System in this part. You should definitely read again whatever you type in here.
5. To conclude your form, this particular segment requires some extra blank fields. Entering I understand and agree to follow, Date, Users Signature Check here for, subject to inspection, Note All EIV system users are, and HUD prior to accessing the system will certainly conclude the process and you can be done in a short time!

Step 3: Check that your details are correct and simply click "Done" to conclude the project. Right after registering a7-day free trial account with us, you will be able to download 2013 or send it via email directly. The file will also be readily accessible from your personal account with all your changes. FormsPal ensures your information privacy via a protected method that in no way records or distributes any type of personal information used in the PDF. Feel safe knowing your paperwork are kept confidential any time you use our services!