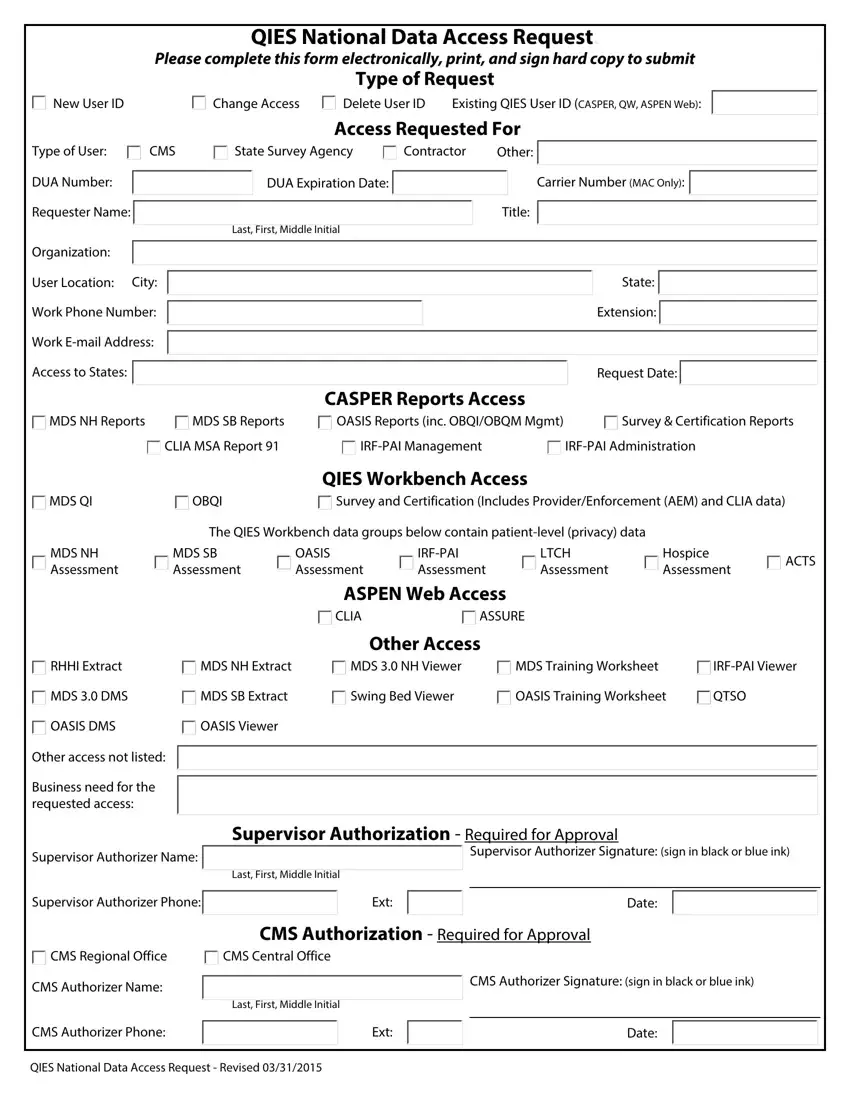
QIES National Data Access Request.
Please complete this form electronically, print, and sign hard copy to submit
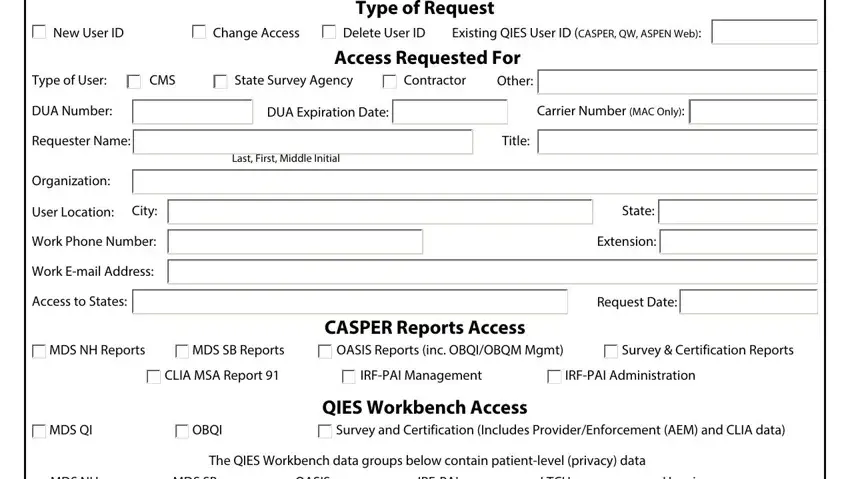
Type of Request
Delete User ID |
Existing QIES User ID (CASPER, QW, ASPEN Web): |
Type of User: |
CMS |
State Survey Agency |
Contractor |
DUA Number: |
|
|
|
DUA Expiration Date: |
|
|
|
|
|
Requester Name: |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
Last, First, Middle Initial |
|
Other: 
Carrier Number (MAC Only): 
Title:
Organization:
User Location: City: Work Phone Number: Work E-mail Address: Access to States: 
CASPER Reports Access
MDS NH Reports |
MDS SB Reports |
OASIS Reports (inc. OBQI/OBQM Mgmt) |
Survey & Certification Reports |
|
CLIA MSA Report 91 |
IRF-PAI Management |
IRF-PAI Administration |

 MDS QI
MDS QI
MDS NH Assessment
QIES Workbench Access
|
OBQI |
Survey and Certification (Includes Provider/Enforcement (AEM) and CLIA data) |
|
|
The QIES Workbench data groups below contain patient-level (privacy) data |
|
|
|
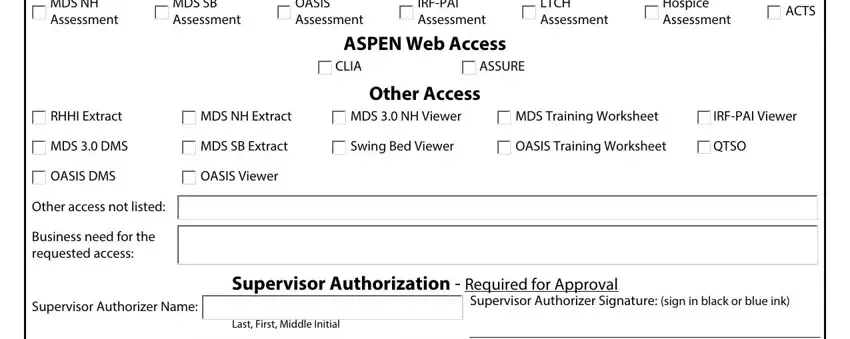
MDS SB |
OASIS |
IRF-PAI |
LTCH |
Hospice |
ACTS |
|
Assessment |
Assessment |
Assessment |
Assessment |
Assessment |
|
|
ASPEN Web Access
Other Access
RHHI Extract |
MDS NH Extract |
MDS 3.0 NH Viewer |
MDS Training Worksheet |
IRF-PAI Viewer |
MDS 3.0 DMS |
MDS SB Extract |
Swing Bed Viewer |
OASIS Training Worksheet |
QTSO |
OASIS DMS |
OASIS Viewer |
|
|
|
Other access not listed: |
|
|
|
|
|
|
|
|
Business need for the |
|
|
|
|
|
|
|
|
|
|
|
|
requested access: |
|
|
|
|
|
|
|
|
|
|
Supervisor Authorization - |
Supervisor Authorizer Name: |
|
|
|
|
|
|
|
|
Last, First, Middle Initial |
|
|
|
|
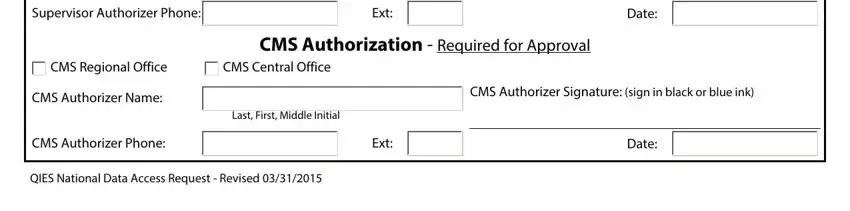
Supervisor Authorizer Phone: |
|
Ext: |
|
|
|
|
|
Required for Approval
Supervisor Authorizer Signature: (sign in black or blue ink)
Date:
 CMS Regional Office CMS Authorizer Name:
CMS Regional Office CMS Authorizer Name:
CMS Authorizer Phone:
CMS Authorization - Required for Approval

 CMS Central Office
CMS Central Office
CMS Authorizer Signature: (sign in black or blue ink)
Last, First, Middle Initial
QIES National Data Access Request - Revised 03/31/2015
PRIVACY ACT ADVISORY STATEMENT
Privacy Act of 1974, P.L. 93-579
The information on side 1 of this form is collected and maintained under the authority of Title 5 U.S. Code, Section 552a(e)(10). This information is used for assigning, controlling, tracking and reporting authorized access to and use of CMS’s computerized information and resources. The Privacy Act prohibits disclosure of information from records protected by the stature, except in limited circumstances.
The information you furnish on this form will be maintained in the Individuals Authorized Access to the Centers for Medicare & Medicaid Services (CMS) Data Center System of Records and may be disclosed as a routine use disclosure under the routine uses established for this system as published at 59 FED. REG. 41329 (08-11-94) and as CMS may establish in the future by publication in the Federal Register.
SECURITY REQUIREMENTS FOR USERS OF CMS COMPUTER SYSTEMS
CMS uses computer systems that contain sensitive information to carry out its mission. Sensitive information is any information which the loss, misuse, or unauthorized access to, or modification of could adversely affect the national interest, or the conduct of Federal programs, or the privacy to which individuals are entitled under the Privacy Act. To ensure the security and privacy of sensitive information in Federal systems, the Computer Security Act of 1987 requires agencies to identify sensitive computer systems, conduct computer security training, and develop computer security plans. CMS maintains a system of records for use in assigning, controlling, tracking and reporting authorized access to and use of CMS computerized information and resources. CMS records all access to its computer systems and conducts routine reviews for unauthorized access to and/or illegal activity.
Anyone with access to CMS Computer Systems containing sensitive information must abide by the following:
-Do not disclose or lend your IDENTIFICATION NUMBER AND/OR PASSWORD to someone else. They are for your use only and will serve as your “electronic signature”. This means that you may be held responsible for the consequences of unauthorized or illegal transactions.
-Do not browse or use CMS data files for unauthorized or illegal purposes.
-Do not use CMS data files for private gain or to misrepresent yourself or CMS.
-Do not make any disclosure of CMS data that is not specifically authorized.
-Do not duplicate CMS data files, create sub files of such records, remove or transmit data unless you have been specifically authorized to do so.
-Do not change, delete, or otherwise alter CMS data files unless you have been specifically authorized to do so.
-Do not make copies of data files, with identifiable data. Or data that would allow individual identities to be deduced unless you have been specifically authorized to do so.
-Do not intentionally cause corruption or disruption of CMS data files.
A violation of these security requirements could result in termination of systems access privileges and/or disciplinary/ adverse action up to and including removal from Federal Service, depending upon the seriousness of the offense. In addition, Federal, State and/or local laws may provide criminal penalties for any person illegally accessing or using a Government-owned or operated computer system illegally.
If you become aware of any violation of these security requirements or suspect that someone else may have used your identification number or password, immediately report that information to your security officer.
Signature of User: (sign in black or blue ink) |
Date: |
Printed User's Name:




 State:
State:  Extension:
Extension: 


 MDS QI
MDS QI CMS Regional Office CMS Authorizer Name:
CMS Regional Office CMS Authorizer Name:
 CMS Central Office
CMS Central Office
