Clear/Reset
Direct Deposit/Automatic Payments
Set-up Guide
Information to help you arrange automatic deposits or payments to/from third parties
How to take advantage of the fastest, and most convenient and secure way to manage receiving regular deposits to, or making regular payments from your account.
Key Benefits of Direct Deposit:
Direct Deposit is a free service that automatically deposits qualifying recurring income* into any Wells Fargo checking, savings, or prepaid card account you choose.
•Convenient – Your money is deposited into your account, even when you are ill, on vacation or too busy to get to the bank.
•Fast – You have immediate access to your money on the day of deposit
•Safe – You never have to worry about checks getting lost, delayed or stolen.
•Opportunity for automatic saving – You can watch your savings grow by directing at least part of your pay to a savings account
*Income you receive from your employer, Social Security, pension and retirement plans, the Armed Forces, VA Benefits, and annuity or dividend payments may all qualify for Direct Deposit.
Key Benefits of automatic payments:
Never worry about missing a payment or possible late fees or other consequences. You will need to have the required available funds in your account at the time of the payment. Note that you can also make recurring payments through Wells Fargo Online with Bill Pay.
Step 1. Gather and Review Account Information
Key information about you and your Wells Fargo account that will allow transactions with third parties to occur:
(1)Your name ________________________________________________________
(2)Routing/Transit Number (9 digits) _______________________________________
(3)Account number (maximum 15 digits, include any leading zeros,
do not include check number __________________________________________
(4) Type of Account (check one) |
Checking/Prepaid Card** |
Savings |
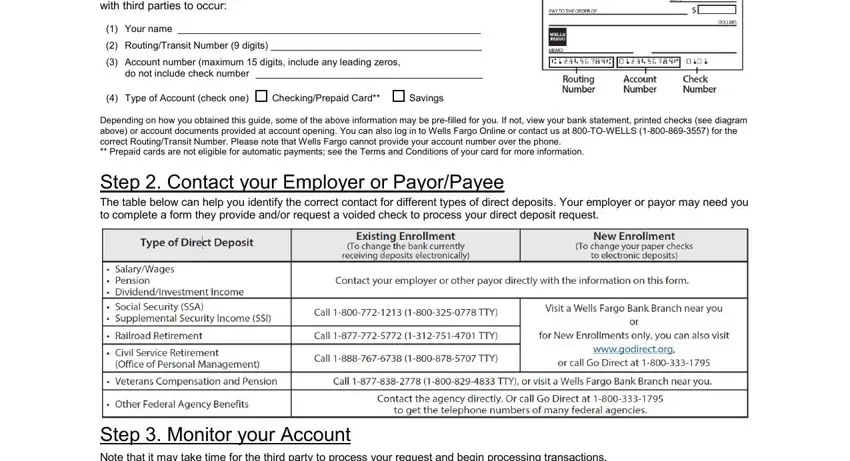
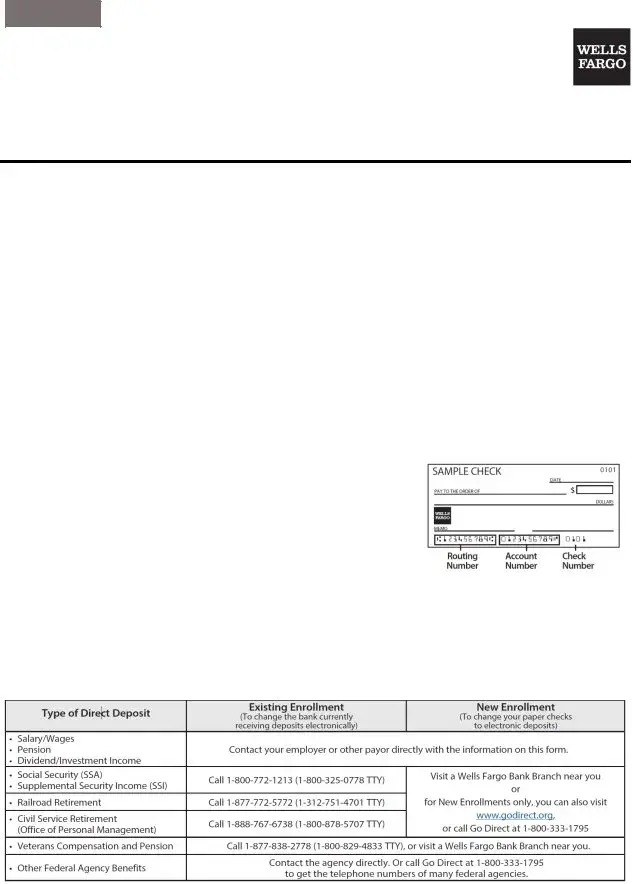
Depending on how you obtained this guide, some of the above information may be pre-filled for you. If not, view your bank statement, printed checks (see diagram above) or account documents provided at account opening. You can also log in to Wells Fargo Online or contact us at 800-TO-WELLS (1-800-869-3557) for the correct Routing/Transit Number. Please note that Wells Fargo cannot provide your account number over the phone.
** Prepaid cards are not eligible for automatic payments; see the Terms and Conditions of your card for more information.
Step 2. Contact your Employer or Payor/Payee
The table below can help you identify the correct contact for different types of direct deposits. Your employer or payor may need you to complete a form they provide and/or request a voided check to process your direct deposit request.
Step 3. Monitor your Account
Note that it may take time for the third party to process your request and begin processing transactions. Questions?: Call us at 1-800-TO-WELLS (1-800-869-3557)
Office Use Only: RTN: {{OC:ADO:Account RTN CHK}} Account Number {{OC:ADO:Account RTN CHK}} |
|
© 2021 Wells Fargo Bank, N.A. All Rights Reserved. Member FDIC. |
|
CNS3519 (Rev 03 – 05/21) |
Page 1 of 1 |