Our PDF editor works to make filling out documents stress-free. It is really not hard to change the [FORMNAME] form. Keep to these particular actions if you want to do it:
Step 1: The first step should be to hit the orange "Get Form Now" button.
Step 2: Now, you are on the form editing page. You may add content, edit present information, highlight particular words or phrases, put crosses or checks, add images, sign the document, erase unnecessary fields, etc.
To be able to create the dd form 2875 fillable PDF, provide the information for each of the segments:
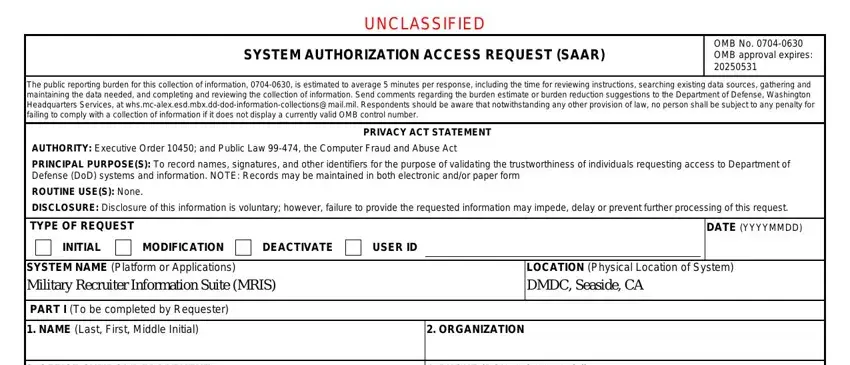
Provide the requested particulars in the field OFFICE SYMBOLDEPARTMENT, PHONE DSN or Commercial, OFFICIAL EMAIL ADDRESS, JOB TITLE AND GRADERANK, OFFICIAL MAILING ADDRESS, CITIZENSHIP, DESIGNATION OF PERSON, MILITARY, CIVILIAN, OTHER, CONTRACTOR, IA TRAINING AND AWARENESS, I have completed the Annual Cyber, DATE YYYYMMDD, and USER SIGNATURE.

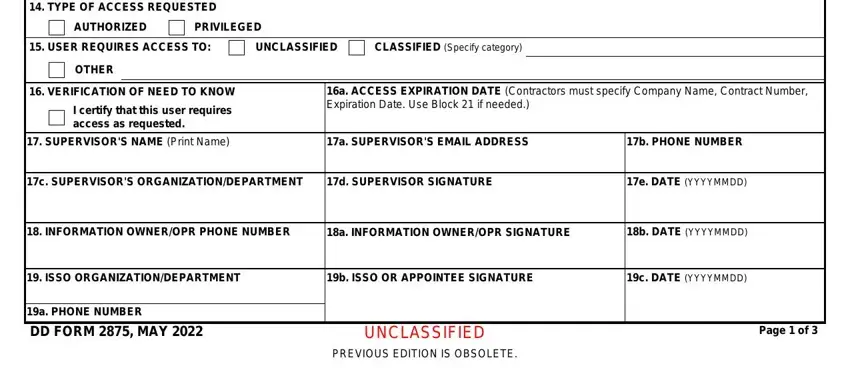
The application will require data to effortlessly prepare the box TYPE OF ACCESS REQUESTED, AUTHORIZED, PRIVILEGED, USER REQUIRES ACCESS TO, UNCLASSIFIED, CLASSIFIED Specify category, OTHER, VERIFICATION OF NEED TO KNOW, I certify that this user requires, a ACCESS EXPIRATION DATE, SUPERVISORS NAME Print Name, a SUPERVISORS EMAIL ADDRESS, b PHONE NUMBER, c SUPERVISORS, and d SUPERVISOR SIGNATURE.
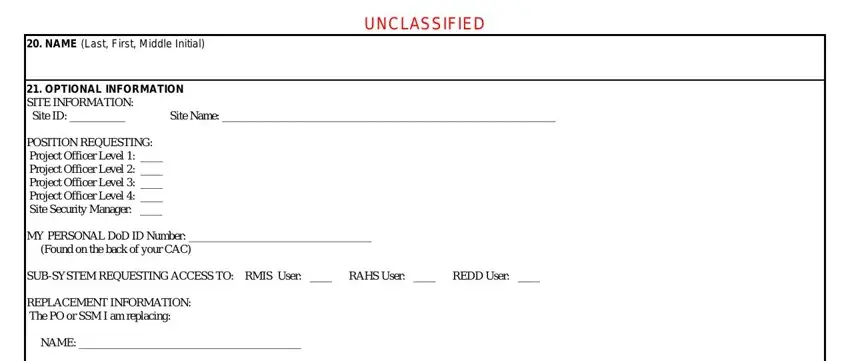
The space NAME Last First Middle Initial, and OPTIONAL INFORMATION is for you to add each side's rights and obligations.
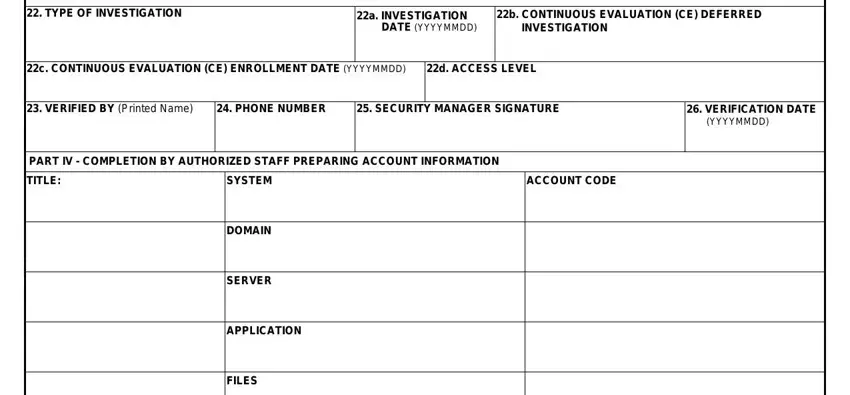
Finalize by reviewing the following sections and submitting the required details: PART III SECURITY MANAGER, TYPE OF INVESTIGATION, a INVESTIGATION, DATE YYYYMMDD, b CONTINUOUS EVALUATION CE DEFERRED, INVESTIGATION, c CONTINUOUS EVALUATION CE, d ACCESS LEVEL, VERIFIED BY Printed Name, PHONE NUMBER, SECURITY MANAGER SIGNATURE, VERIFICATION DATE, YYYYMMDD, PART IV COMPLETION BY AUTHORIZED, and ACCOUNT CODE.
Step 3: Press the button "Done". Your PDF document may be exported. It is possible to obtain it to your laptop or email it.
Step 4: Ensure that you prevent potential problems by preparing minimally a pair of copies of your form.