You must document every detail accurately to manage the response to a security incident. To complete the form, open the security incident report example (PDF) in our editor.
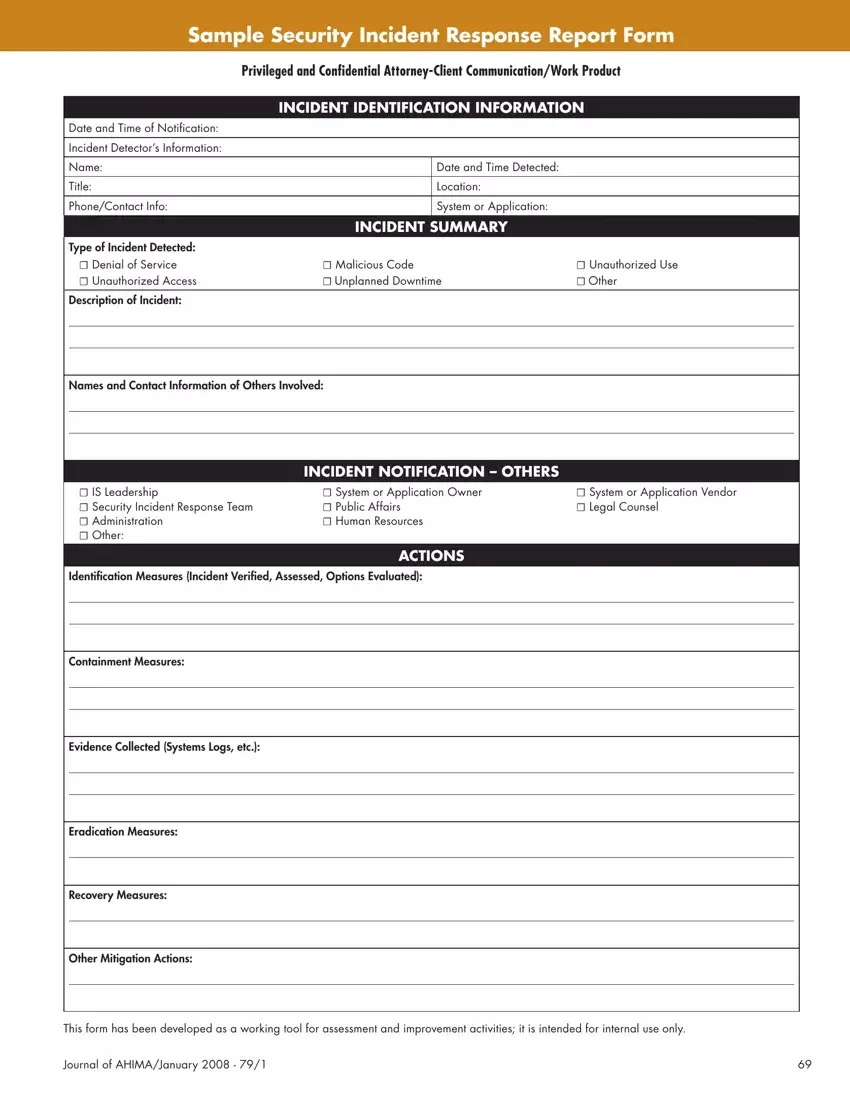
1. Incident Identification Information
Write the date and time when the incident was first noticed and officially reported. It helps establish a timeline. Provide the name, title, location, contact information, and system or application details of the person who detected the incident.

2. Incident Summary
Describe the type of incident, selecting from options like "Denial of Service," "Malicious Code," "Unauthorized Use," "Unauthorized Access," "Unplanned Downtime," or other relevant categories.
Provide a detailed description of what happened, including the exact nature and scope of the incident. Also, list the names and contact details of other individuals involved, which might include witnesses or those affected by the incident.

3. Incident Notification – Others
Indicate which parties within and outside the organization have been notified about the incident. This part might include "IS Leadership," "System Owners," "Vendors," the "Security Incident Response Team," "Public Affairs," "Legal Counsel," "Administration," and "Human Resources."
4. Actions
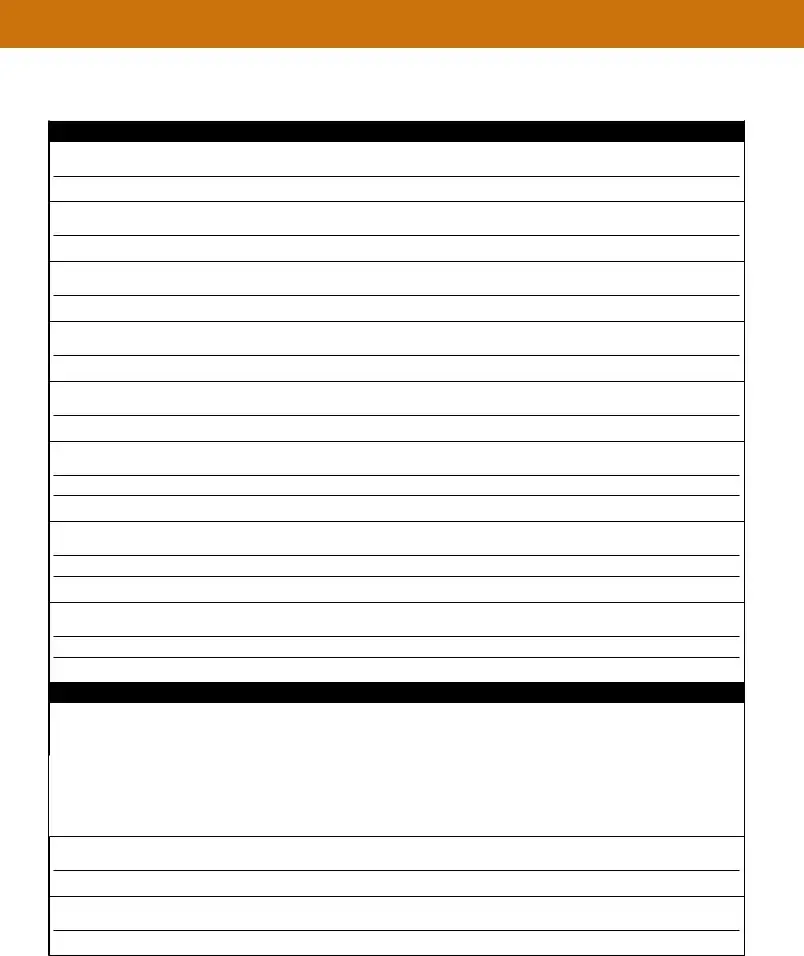
Document the immediate actions taken following the incident. It includes how the incident was verified, the assessment of the situation, and the options evaluated.
Detail the containment measures to prevent further damage, the evidence collected such as system logs, the eradication measures to remove the threat, and the recovery steps to bring systems back online. Also, note any other mitigation actions taken to secure the environment.

5. Evaluation
Evaluate how well the workforce responded to the incident. Assess if the documented procedures were followed and if they were adequate. Reflect on what information was needed sooner and any steps or actions that might have inhibited recovery.

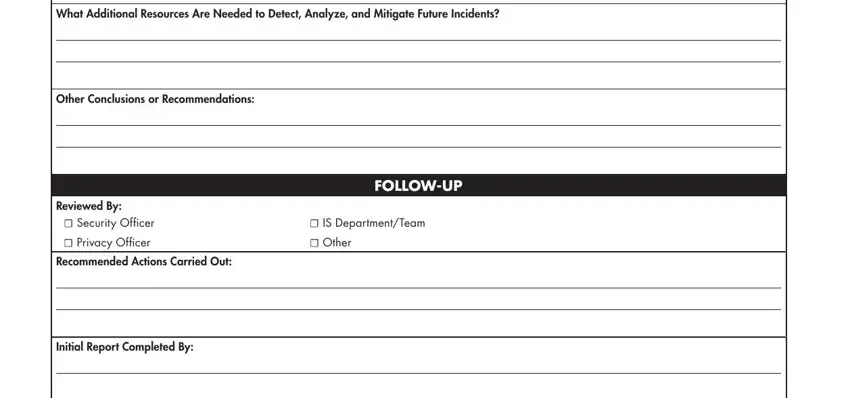
6. Follow-Up
In the final section, document any reviews conducted post-incident, including who reviewed the incident report and the recommended actions that were carried out. Indicate who completed the initial report and who was responsible for the follow-up.
Filling out this form carefully is crucial for managing the current situation and planning future security precautions.