Working with PDF files online is actually surprisingly easy with our PDF tool. You can fill in va handbook 6500 6 here effortlessly. To have our editor on the leading edge of practicality, we work to put into operation user-driven capabilities and enhancements regularly. We are routinely looking for feedback - assist us with remolding PDF editing. With some basic steps, it is possible to begin your PDF editing:
Step 1: Open the PDF doc in our editor by clicking the "Get Form Button" in the top part of this webpage.
Step 2: This editor will give you the capability to work with the majority of PDF forms in a range of ways. Modify it by writing any text, correct what's originally in the document, and add a signature - all at your fingertips!
As for the fields of this precise PDF, here is what you want to do:
1. To get started, when filling out the va handbook 6500 6, start with the section containing following blanks:

2. After filling in the previous part, head on to the subsequent part and fill out the necessary details in all these blanks - Reference HANDBOOK APPENDIX A, Is this an acquisition or purchase, Yes, Does the contract involve VA, See PROCEDURES a If yes proceed, Yes, Will this acquisition require, and personnel If no proceed to.
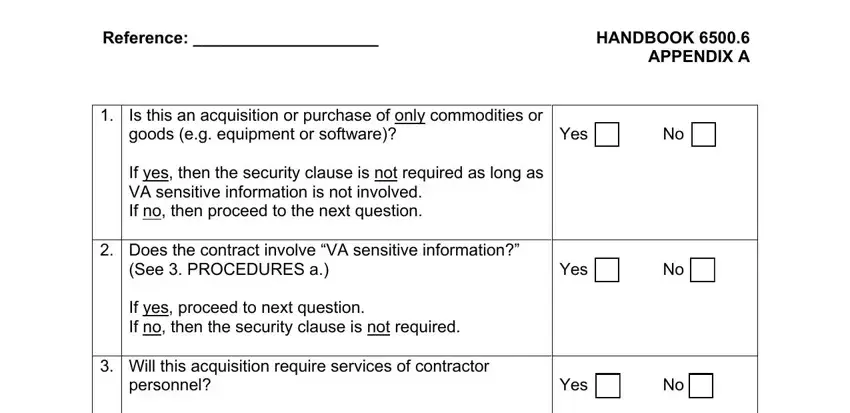
3. Completing Yes, personnel If no proceed to, Will the personnel perform a, and access to a VA system or VA is essential for the next step, make sure to fill them out in their entirety. Don't miss any details!

4. It's time to proceed to the next portion! Here you'll get all of these Reference HANDBOOK APPENDIX A, Yes Yes Yes Yes Yes, Will this acquisition require use, Information Technology IT system, next question, and If yes then VA security policies blanks to fill out.
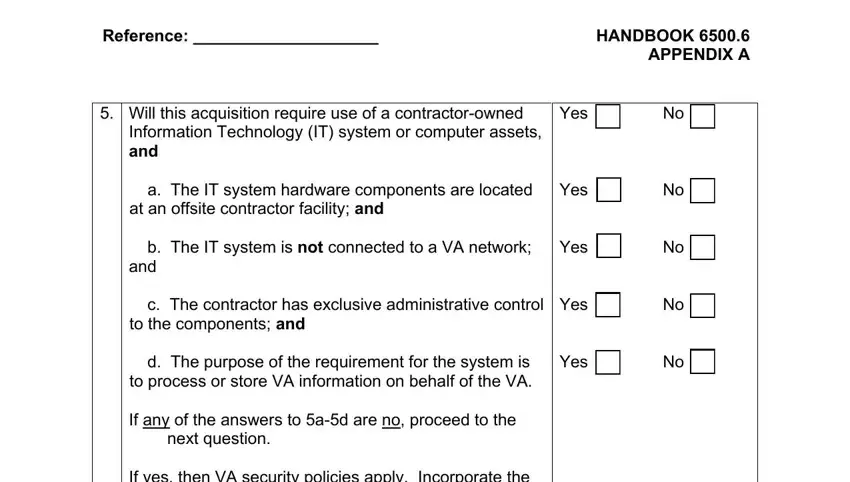
5. This form must be wrapped up by dealing with this segment. Below you can see an extensive set of form fields that have to be filled in with specific details for your document usage to be faultless: Reference HANDBOOK APPENDIX A, Yes, requirements, Ensure yearly FISMA assessments, and uploaded into SMART, Will this acquisition require, and connection of one or more.
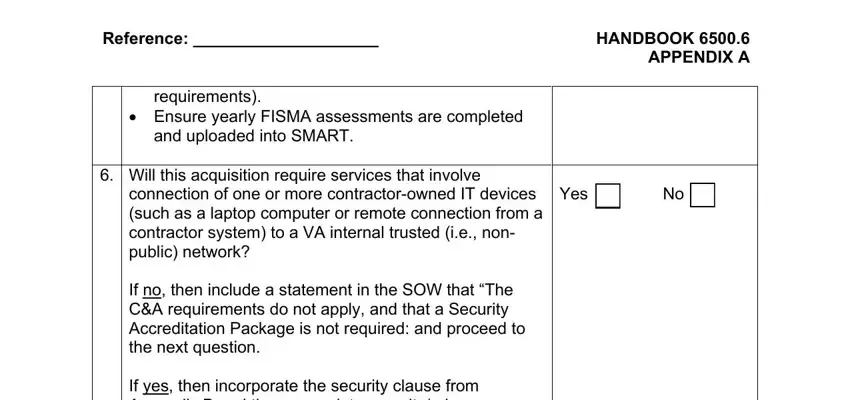
As to and uploaded into SMART and Yes, ensure that you take another look here. These two are the most significant fields in this file.
Step 3: Prior to moving on, you should make sure that all form fields were filled in the right way. When you’re satisfied with it, press “Done." Right after setting up afree trial account here, you will be able to download va handbook 6500 6 or send it through email promptly. The document will also be at your disposal in your personal account page with all of your modifications. Here at FormsPal, we aim to be sure that your information is kept protected.