When using the online tool for PDF editing by FormsPal, you'll be able to fill out or alter CATEGORIES here and now. We at FormsPal are committed to providing you the absolute best experience with our editor by constantly introducing new functions and improvements. With these updates, using our editor gets better than ever! Starting is simple! What you need to do is stick to the next basic steps directly below:
Step 1: Just press the "Get Form Button" at the top of this page to access our pdf file editor. Here you will find everything that is needed to work with your document.
Step 2: The tool will allow you to customize PDF files in a variety of ways. Modify it by adding personalized text, correct what's originally in the PDF, and put in a signature - all when it's needed!
It is easy to complete the document using out detailed tutorial! Here's what you have to do:
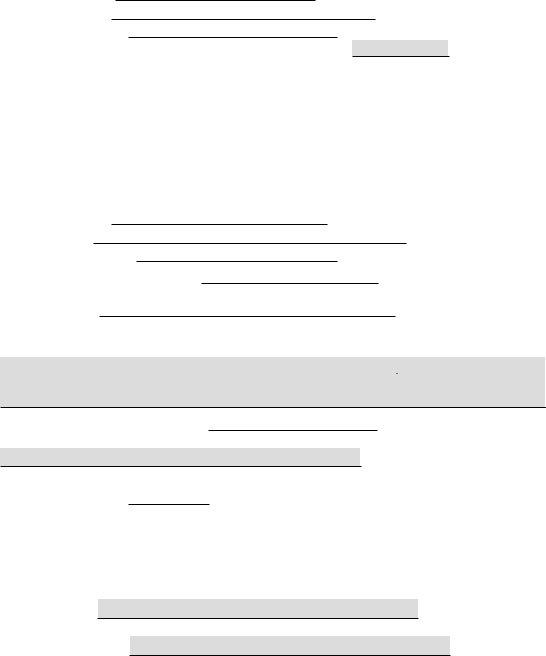
1. Whenever completing the CATEGORIES, be certain to incorporate all necessary fields within the relevant section. This will help to speed up the process, which allows your details to be processed fast and properly.
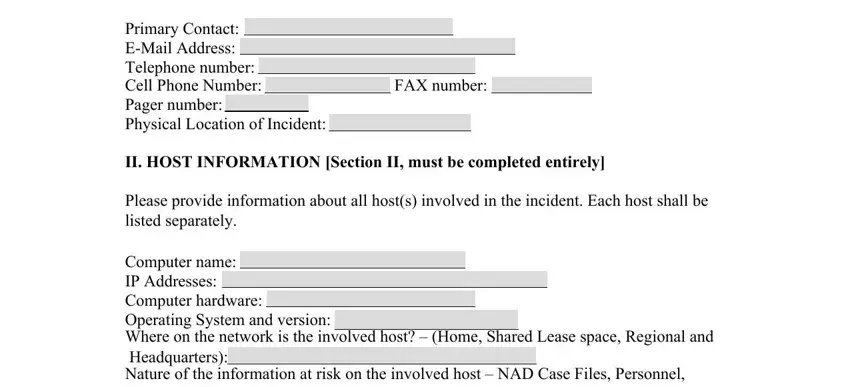
2. Given that the previous array of fields is completed, it is time to include the required details in Computer name IP Addresses, Time zone of the involved host Was, Was this host compromised as a, Yes, III INCIDENT CATEGORIES, All categories applicable to the, Data Losses, Hardware Losses, and Yes Intruder gained access so that you can move on further.
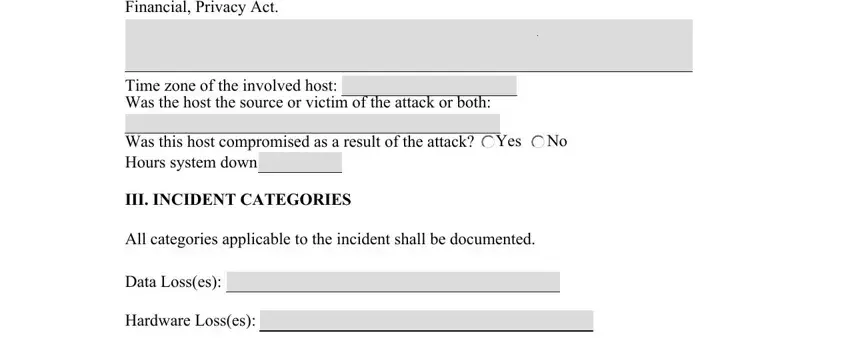
It is possible to make an error while filling in the III INCIDENT CATEGORIES, so make sure you reread it before you send it in.
3. The following step is all about Yes Intruder gained access, and Form NAD - fill out each of these blank fields.
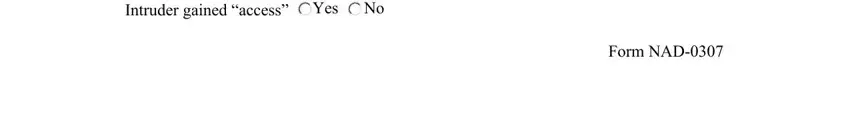
4. Your next subsection needs your information in the subsequent areas: Cracked password Easilyguessable, Yes, No Yes Yes, No No, IV SECURITY TOOLS, At the time of the Incident was, Yes, AuthenticationPassword tools, Were logs being maintained If so, V DETAILED INCIDENT DESCRIPTION, and Detailed Incident Description This. Be sure to fill out all of the needed information to go forward.
5. To conclude your form, the particular area incorporates a number of extra fields. Filling in A Duration of Incident, B How was the incident discovered, C Methods used by intruders to, D Detailed discussion of, and E Hidden filesdirectories should finalize the process and you can be done in a snap!

Step 3: You should make sure the information is accurate and press "Done" to continue further. Make a 7-day free trial plan with us and acquire instant access to CATEGORIES - readily available inside your FormsPal account page. FormsPal is focused on the personal privacy of all our users; we always make sure that all personal information going through our editor continues to be secure.